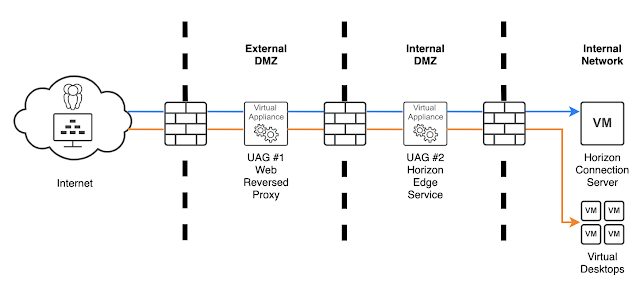
When you have a double dmz environment, you want to address an extra-layer of security. You can deploy a Unified Access Gateway on the outer-layer DMZ zone and utilize the Reverse Proxy feature.
All traffic will proxied through External DMZ's UAG. By doing this, you will achieve better security for your users from the internet. However, bare in mind the caveat is, it might impact your performance because there is a additional hop introduced.
Now we take a look how do we configure this.
***Note: The guides explained in this post are experimented in a LAB environment.***
All traffic will proxied through External DMZ's UAG. By doing this, you will achieve better security for your users from the internet. However, bare in mind the caveat is, it might impact your performance because there is a additional hop introduced.
Now we take a look how do we configure this.
***Note: The guides explained in this post are experimented in a LAB environment.***
- Deploy UAG #1 in your External DMZ environment with the forward rules configuration during your appliance OVF deployment. The forward rules allows the authentication and display protocol traffic to be forwarded from UAG#1 to UAG#2.
- At the forward rules configuration, specify the IP address of the UAG#2
- Once the UAG appliance deployment is finished, login to the admin portal, enable "Edge Service Settings" and configure "Reverse Proxy Settings"
- Once complete, save it and move on to configure UAG#2 at the Internal DMZ.
- Login to the admin portal, enable "Edge Service Settings" and configure "Horizon Settings"
- Once complete, save it. If you want to test, login to your virtual desktop and shut down UAG#1. You will get disconnected. Power up UAG#1, login again to your virtual destkop and this time shutdown UAG#2. You will get disconnected again. This demonstrate that the traffic is passing through UAG#1 and UAG#2.
"Proxy Destination URL" is the UAG#2 FQDN address.
"Proxy Destination URL Thumbprints" is the UAG#2 certificate thumbprint.
"Proxy Pattern" can be the same pattern as the UAG#2
"PCOIP External URL" is the UAG#1 IP address.
"BLAST External URL" is the UAG#1 FQDN address.
"Tunnel External URL" is the UAG#1 FQDN address.





Comments
Post a Comment